Digital Safety Reference Guide for 2025
Signal Configuration
Signal is an open-source communication app which leverages end-to-end encryption to protect your data. Signal can be used for direct messages, group chats, sharing files, and even video calls.
Keeping Communications Confidential
- prioritize using Signal - Emails, text messages, and video conferencing software are not secure. These methods of communication are frequently exploited to track users. As a matter of forming good habits (and for your personal privacy), we recommend using Signal or related end-to-end communications whenever possible.
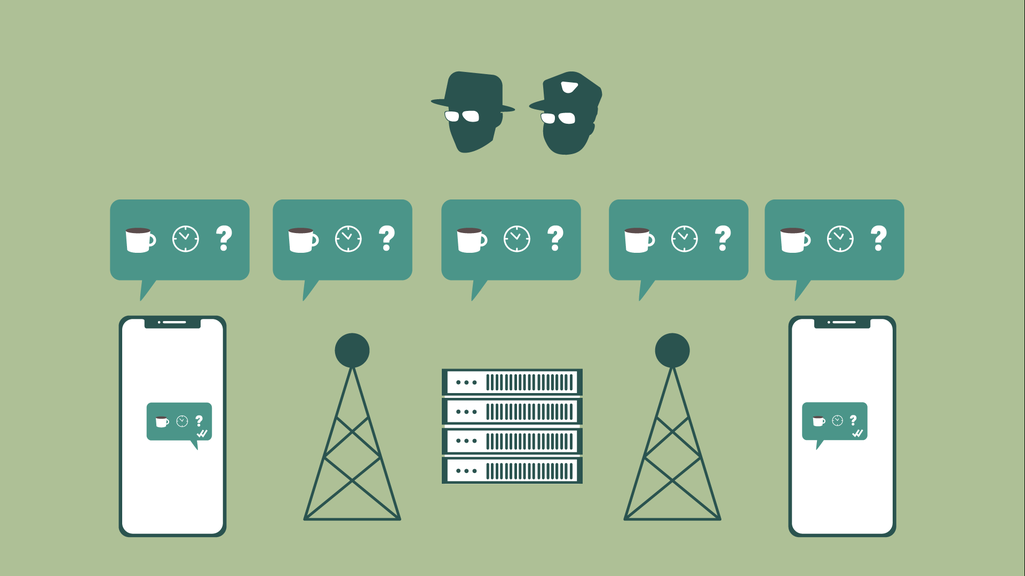
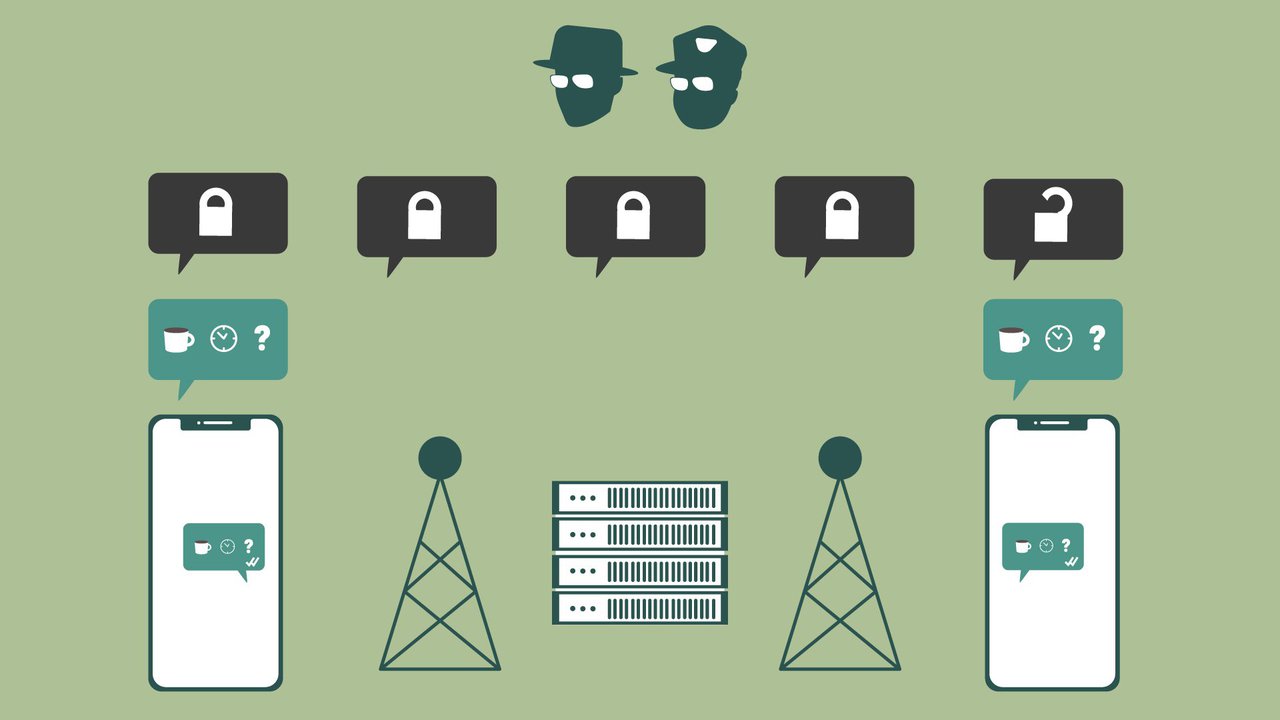
unencrypted messages can be read by private entities and law enforcement
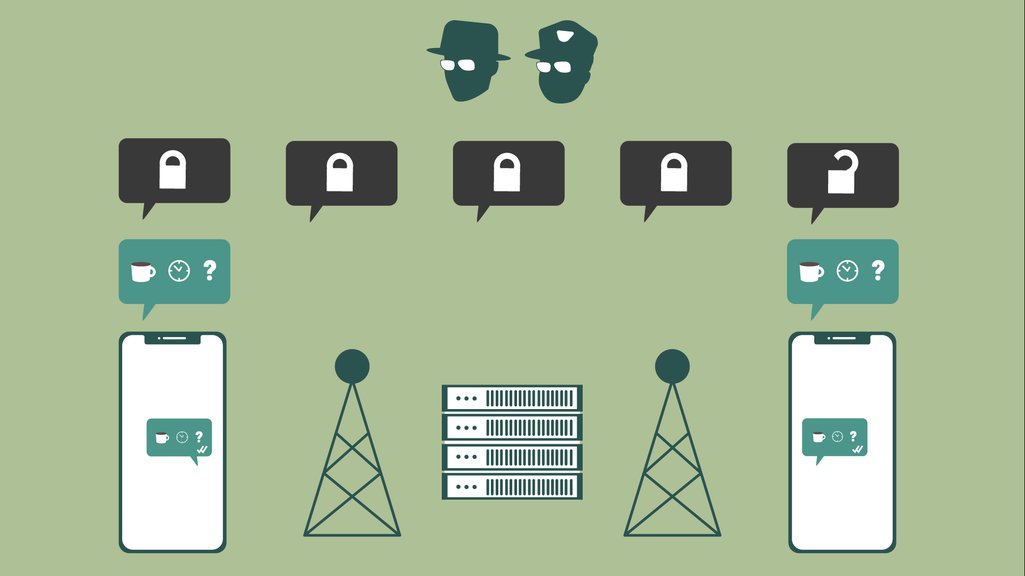
encrypted messages lock-down their content - preventing anyone between either endpoint from reading the message
Having a Zoom call to discuss an Action? Move it to Signal. Want to share your new poster design? Those files/photos can be sent over Signal too.
- use 'Disappearing Messages' - Signal can be setup to automatically delete old messages that you no longer need anymore. Data which does not exist cannot be used against you. If, in another few weeks, you will have no need to re-read today's messages - then you do not need to store today's messages. By default, we recommend setting Disappearing Messages to 4 weeks.
open your chat >> tap-on the user icon (top-left corner) >> select Disappearing Messages >> chose a time which works best for your conversation - hide ''Notification Content' - Can you read new messages from your phone’s lock screen (eg: before you type-in the pin)? It’s fine if you can - but remember that those Notifications Settings are not ideal for hiding Signal messages. Conveniently, Signal allows you to configure the app's notifications so that message content is hidden.
in Signal, navigate to Settings >> Notifications >> Notification Content - then select the option which works best for you
Identity Protection
- refrain from using your Full Name - No one who you're communicating with on Signal needs to constantly be able to see your first and last names. We recommend just using your first name and a last initial - or alternatively, maybe use a pseudonym.
- consider hiding your phone number - Signal allows you to connect with other users via Signal username... or your phone number. Your phone number, however, already exists in all sorts of public databases and can easily be linked to you. Whenever possible, try to use Signal usernames when finding accounts to message.
Phone Number Privacy: in Signal, navigate to Settings >> Privacy >> Phone Number
Find Username: in Signal: navigate to Settings >> look at your Profile details >> find your username (it will match pattern 'name.##' - eg 'rebel.12')
Further Reading:
- Surveillance Self-Defense - How to Use Signal
- Digital Rights Bytes - Can the Government Read my Text Messages
- Activist Checklist - Signal Security Checklist
Secure Social Media Tips
Social media is an incredibly powerful tool that allows basically everyone with an Internet connection to share information. Regrettably, some of the shared information may be used against you - or powers that be may try to silence your voice.
Anonymity
- Decide early-on whether you want your account to be explicitly tied to your online identity or if you would prefer to use a pseudonym. There are pros and cons to either approach – but its best to make an intentional decision sooner rather than later.
(and even if a social media account is tied to your identity - you should still be cautious about what your online identity is and what is publicly known about you) - never post photos of other rebels without their EXPLICIT permission - You do not know what their risk model is, other activist groups they may be involved with, or which threats you may accidentally expose them to. Please be careful with any/all photos you have (Signal actually has a handy face-blurring tool).
Resilience
- Multi-Factor Authentication - Account takeovers do happen - including for activist social media accounts - configure Multi-Factor Authentication (also called MFA or two-factor) to help protect your accounts. Configurations to enable MFA can typically be found in a platform's Security/Privacy Settings.
- reference backup lines of communication - In your profile’s description and other posts, be sure to include links to other social media accounts or websites that you control. This way, you can still communicate if a service goes-down or you lose access to an account. Additionally, you will be further-protected from account impersonation.
- consider restricting access - Depending on what you use your social media presence for, you may prefer to just make your posts private or restrict who can comment. The Internet is... it’s not a good place. Take care of yourself!
Further Reading:
- CISA (yes we are referencing a DHS agency, Director Easterly was awesome) - More than a Password
- Surveillance Self-Defense - Protecting Yourself on Social Networks
Featured:
-
The third annual Week of Rebellion is full of opportunities for celebration and action!
-
Our government had the opportunity to finally turn our state into a "climate leader," and they decided yet again to prioritize profits and political posturing over the well-being of residents.
-
Prominent climate scientists and activists demand immediate climate action in the United States.
-
Stop the Fossil Fuel Industry, Now: List of events for Extinction Rebellion Boston's September week of rebellion
-
A compilation of books, movies, articles, and ways to take action to protect Black lives
-
Nadia Colburn, PhD and member of Extinction Rebellion Media team, discusses how to talk about the climate and ecological crisis with family and friends.
Upcoming Events:
-
Wed Mar 4th @ 11 a.m.
-
Thu Mar 5th @ 7:30 p.m.
-
Sat Mar 7th @ 11 a.m.